What is TUNNELING PROTOCOL? What does TUNNELING PROTOCOL mean= TUNNELING PROTOCOL meaning – TUNNELING PROTOCOL definition – TUNNELING PROTOCOL explanation.
Source: Wikipedia.org article, adapted under https://creativecommons.org/licenses/by-sa/3.0/ license.
SUBSCRIBE to our Google Earth flights channel – https://www.youtube.com/channel/UC6UuCPh7GrXznZi0Hz2YQnQ
In computer networks, a tunneling protocol allows a network user to access or provide a network service that the underlying network does not support or provide directly. One important use of a tunneling protocol is to allow a foreign protocol to run over a network that does not support that particular protocol; for example, running IPv6 over IPv4. Another important use is to provide services that are impractical or unsafe to be offered using only the underlying network services; for example, providing a corporate network address to a remote user whose physical network address is not part of the corporate network. Because tunneling involves repackaging the traffic data into a different form, perhaps with encryption as standard, a third use is to hide the nature of the traffic that is run through the tunnels.
The tunneling protocol works by using the data portion of a packet (the payload) to carry the packets that actually provide the service. Tunneling uses a layered protocol model such as those of the OSI or TCP/IP protocol suite, but usually violates the layering when using the payload to carry a service not normally provided by the network. Typically, the delivery protocol operates at an equal or higher level in the layered model than the payload protocol.
To understand a particular protocol stack imposed by tunneling, network engineers must understand both the payload and delivery protocol sets.
As an example of network layer over network layer, Generic Routing Encapsulation (GRE), a protocol running over IP (IP protocol number 47), often serves to carry IP packets, with RFC 1918 private addresses, over the Internet using delivery packets with public IP addresses. In this case, the delivery and payload protocols are the same, but the payload addresses are incompatible with those of the delivery network.
It is also possible to establish a connection using the data link layer. The Layer 2 Tunneling Protocol (L2TP) allows the transmission of frames between two nodes. A tunnel is not encrypted by default, it relies on the TCP/IP protocol chosen to determine the level of security.
SSH uses port 22 to enable data encryption of payloads being transmitted over a public network (such as the Internet) connection, thereby providing VPN functionality. IPsec has an end-to-end Transport Mode, but can also operate in a tunneling mode through a trusted security gateway.
A Secure Shell (SSH) tunnel consists of an encrypted tunnel created through an SSH protocol connection. Users may set up SSH tunnels to transfer unencrypted traffic over a network through an encrypted channel. For example, Microsoft Windows machines can share files using the Server Message Block (SMB) protocol, a non-encrypted protocol. If one were to mount a Microsoft Windows file-system remotely through the Internet, someone snooping on the connection could see transferred files. To mount the Windows file-system securely, one can establish a SSH tunnel that routes all SMB traffic to the remote fileserver through an encrypted channel. Even though the SMB protocol itself contains no encryption, the encrypted SSH channel through which it travels offers security.
To set up a local SSH tunnel, one configures an SSH client to forward a specified local port (green in the images) to a port (purple in the images) on the remote machine (yellow in the image). Once the SSH tunnel has been established, the user can connect to the specified local port (green) to access the network service. The local port (green) does not have to be the same as the remote port (purple).
….
source













![CY_GATE_2019_PHYSICAL_SPECTROSCOPY_[ELECTRONIC_BASIC]_All IN ONE_[Short_Trick]_2018-19_PART_1ST - Videos](https://trends.edugorilla.com/wp-content/uploads/sites/8/2018/08/cy_gate_2019_physical_spectroscopy_electronic_basic_all-in-one_short_trick_2018-19_part_1st-218x150.jpg)








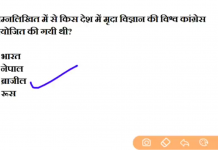






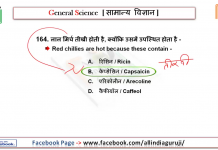


![24 August 2018 – The Indian Express Newspaper Analysis हिंदी में – [UPSC/SSC/IBPS] Current affairs - Videos](https://trends.edugorilla.com/wp-content/uploads/sites/8/2018/08/a520-218x150.png)



